The best ransomware protection for your backup
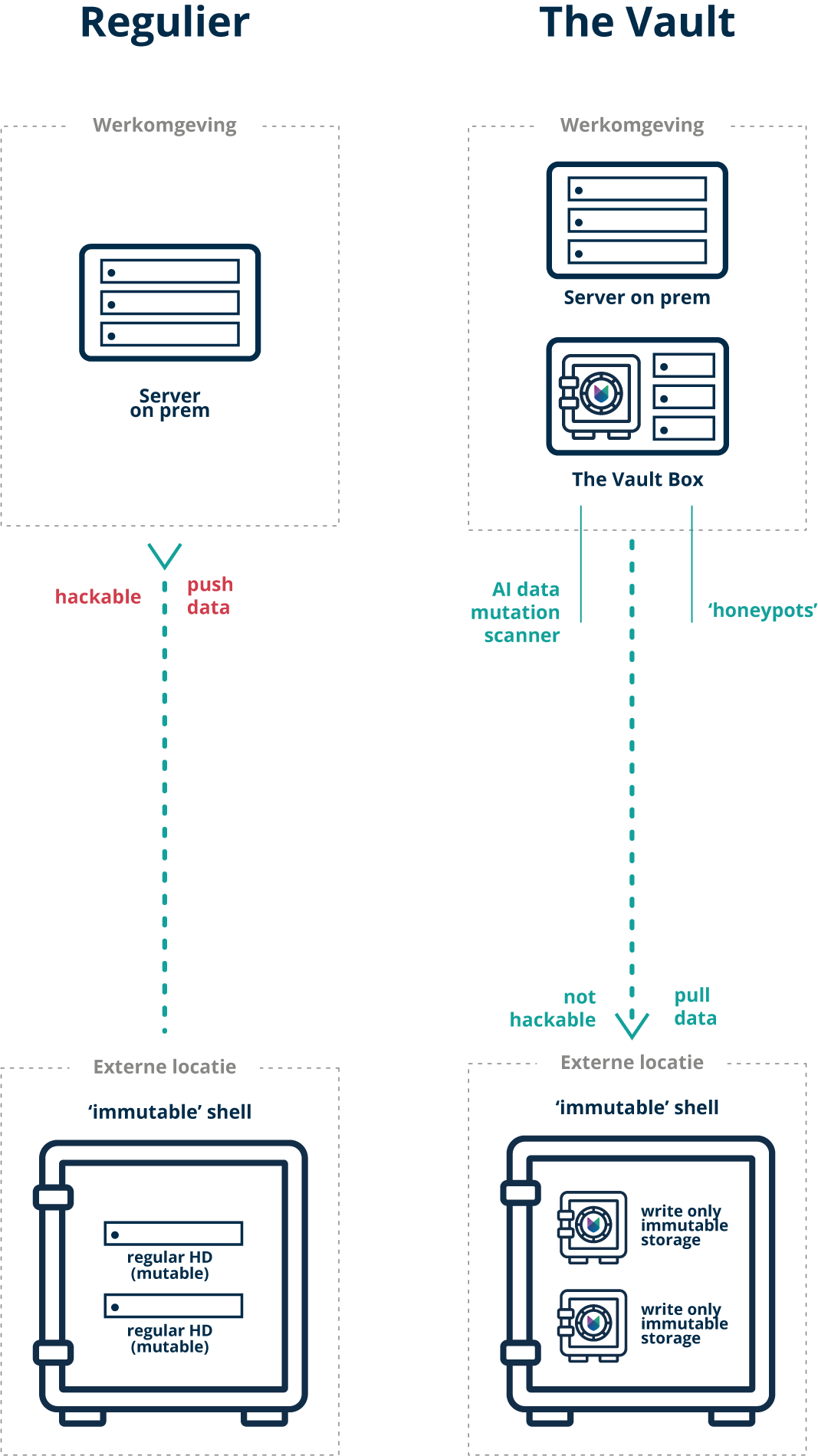
The Vault is an advanced immutable storage that resides in the IMMUTEC Datacenter in the Netherlands and can be compared to a digital bank vault. In that bank vault, we can park encrypted packets of your data. Data cannot be modified and no software (malware) can be started.
Unlike a regular backup, only encrypted, packets of your data can be written away. The Vault is constantly watching for data changes or additions to your backup. If so, a new packet of encrypted data is put into The Vault. Updated actually because the packages already on there are there for good. These – as on a CD-ROM – cannot be changed or deleted in any way. Not even by a hacker.
The Vault
Not just any immutable storage
The Vault is not just any immutable storage but differs from regular immutable storage solutions in a number of crucial ways:
Works with your existing backup system
Because The Vault is an extension or addition, we can implement on virtually any existing backup system. So that means you don’t have to buy additional hard-ware and you don’t have to shake up your entire IT infrastructure. Super convenient! No fuss.
Air-gapped and social engineering proof
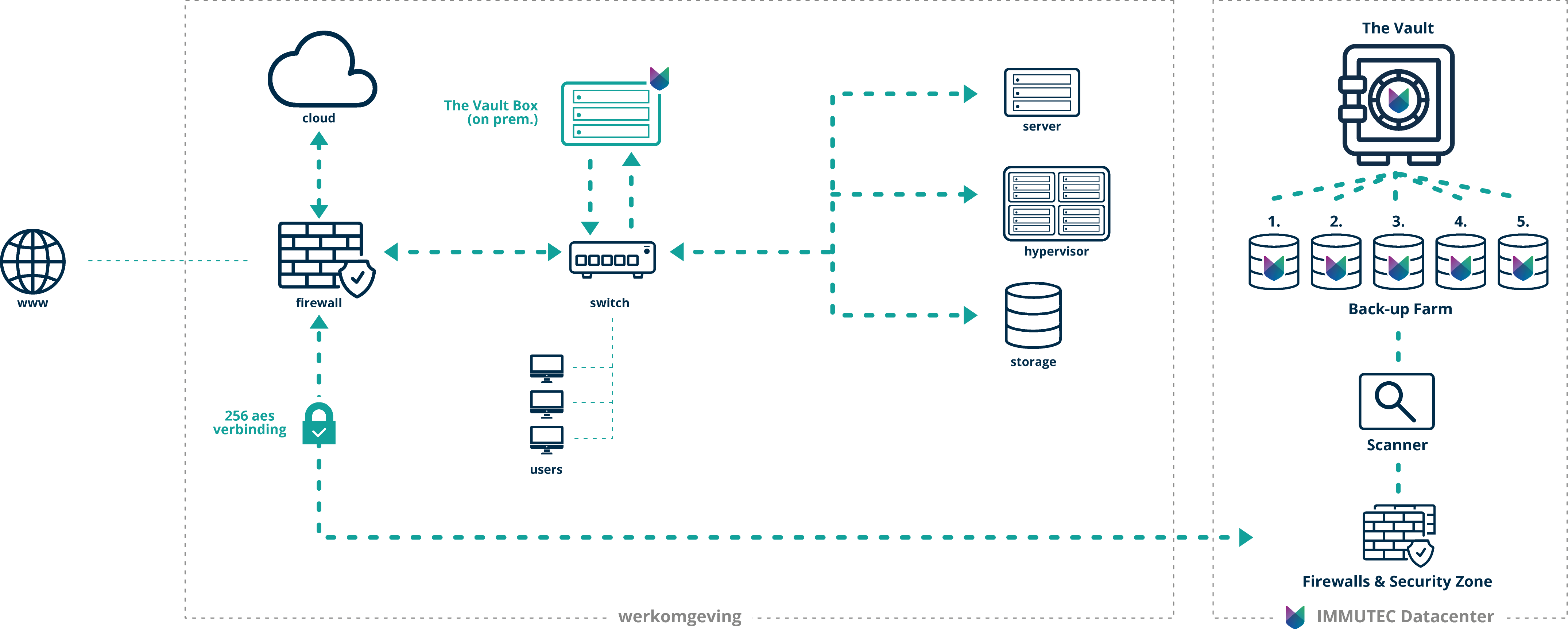
Air-gapped, meaning there is no direct connection between your IT infrastructure and our data vault, The Vault (the Immutable storage). Your data is safely stored in a data center in the Netherlands.
Social engineering: If a hacker is in your network, he usually takes over computers (can watch). So are those of your administrators. Administrators have access to equipment. So the hacker can also access that equipment because he can see the login credentials. Often done by social engineering, the hacker now knows who the administrator is.
As a client, you have no login capability to The Vault, nor does the hacker see the connection. The data center itself sets up the encrypted connection once a day to pull data away to the vault (pull data), then the connection is gone. A regular immutable solution pushed the data from the work environment allowing the hacker to see what is happening.
Low Total Cost of Ownership (TCO).
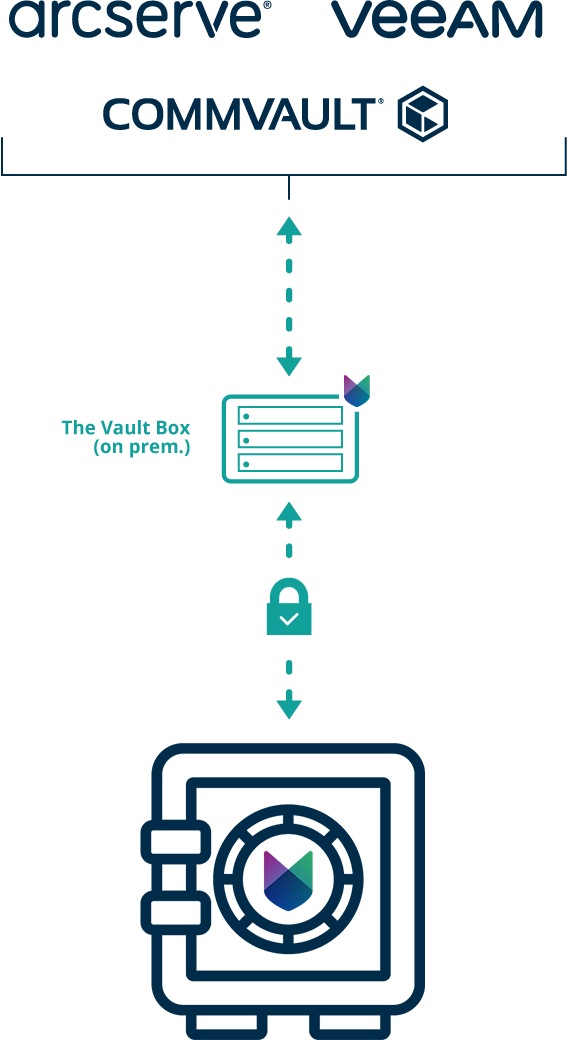
We place additional secure storage (The Vault Box) in your IT infrastructure. You can store your backup files directly on it. No more proprietary hardware required. This saves on your storage capacity and on your investment. This secure storage then connects back to The Vault, the data vault where the data is then finally stored in true security.
Advanced data encryption
When you save the backup data files you put a key on here that you keep yourself. We do not have the key and therefore cannot look into the data that is in the safe, nice for you.
Security development in collaboration with UM
Together with the Department of Advanced Computer Science at Maastricht University, we continue to develop two unique components of the platform.
- Honeypots
Honeypots are “traps” that are placed on The Vault Box at your location. These traps are attractive only to hackers. If a hacker is present in your hardware network, he will be triggered to take a look here. With us, an alarm then immediately goes off, allowing us to alert you and shut off the data additionally. - Encrypted Data Scan
Furthermore, we are developing “scanning and analysis capabilities in encrypted data” with Maastricht University. This allows us to detect hacks and patterns in data we cannot read. The data is protected and also analyzed for you.
Physical immutable (instead of software-based)
In most cases, Immutable Storage is based on software that “runs” on a platform. IMMUTEC’s Immutable platform consists of physical (iron) servers (hardware). This hardware is actually assigned to you. One of the benefits of this is that you are on a very fast storage (storage) environment and thus have high throughput speeds. When you need the data, you can get it at lightning speed.
At IMMUTEC, it is not possible to delete data using software. If data needs to be deleted (only at the customer’s request), this must be done remotely as well as by someone physically at the location (in our secure data center) of the servers.
Pay per use (TB)
Immutable storage is very expensive to purchase. In addition, in many cases you have to buy a large server which means you have to make a large investment. With IMMUTEC, you pay for usage and the premium is calculated based on the amount of data storage you need.
Total care from A to Z
As data protection specialists, we take a piece of worry away from you. We arrange everything for you;
- Maintenance
- Management
- Monitoring
We guard your data until it is needed. Have you lost access to your data due to a disaster or ransomware, for example? In many cases, we have already seen the first signs by then and are already setting up the data on The Vault Box at your location.
Data-on-disk service
High urgency with lots of data? We can also provide the data on a physical hard disk. Other vendors have a platform where you have to download the data (often at slow speeds).
Help AFTER a hacking or ransomware attack
Are you being hacked or the victim of a ransomware attack? Don’t panic, we can help.
Our IR (Incident & Response) partner can immediately help resolve the emergency. They have already helped many clients and have been able to prevent much worse.
Advanced hacker detection
Your data is safe on IMMUTEC’s platform, but we can do more. We can also link detection software to the Azure platform that allows us to provide your endpoints and network with high-quality detection and we can detect hackers quickly, early.
Rapid implementation
After your approval, we will start working for you immediately. Within 2 weeks, you will be connected to The Vault. We only need limited support from your own IT department. We handle the implementation.
Here’s how The Vault fits into your IT infrastructure
Without The Vault:
No guarantee of data return
Directors to be held liable
No cybersecurity insurance coverage
Not AVG & NIS2 compliant
Bankruptcy risk
Image damage
Your data safe in the data center of the Netherlands
Immutec has its own shielded data room with secure servers and segmented security areas in Amsterdam. This is where the IMMUTEC Platform is located. The Datacenter features:
All required certifications: ISO27001, SOC1, SOC2, etc.
22.7 MW hyperscale-ready campus
More than 17,000 square feet of facility
7 data halls
200+ customer ecosystem
50+ networks
AMS-IX and NL-IX internet exchanges.
PUE as low as 1.2
100% renewable energy
FAQ The Vault
What does air-gapped mean?
An “airgapped” system is like a computer that has no Internet and is not connected to other computers. It is physically isolated to provide maximum security against hackers and cyber attacks. These types of systems are used for highly sensitive information, but they have limited capabilities for data exchange with other computers.
What is an Immutable Storage safe?
An “immutable storage vault” is a storage system in which data is stored once and then cannot be changed or deleted for a preset period of time. It is used to retain data permanently and immutably, often for compliance purposes. They provide an additional layer of security and ensure that data is not intentionally or accidentally modified or deleted, even by authorized users.
Is your service The Vault a backup?
No, The Vault is not a backup solution. It complements your backup.
Your backup system backs up. The result of that backup are folders and/or files containing encrypted data. The Vault copies these encrypted data packets and makes them unmodifiable. The data packets are password-protected by you, so someone else cannot extract or read it. Neither do we. What we can do is return the data packages when – after a disaster – your backup system is up and running again.
Why is backup not enough?
A backup solution backs up your files and documents. A hacker’s goal is to make sure that no longer works and that the data in your backup is encrypted or misappropriated. This ensures that you can no longer restore a backup or access your backup system yourself. The only solution you have then is to pay a ransom. Unfortunately, in 9 out of 10 cases, that’s not enough either and it remains to be seen whether all your data will be released again.
Does The Vault replace my backup system?
No, The Vault is not a backup solution. It complements your backup.
The Vault can only do 1 thing: encrypt a backup file (created by your backup package) and store it securely so that it cannot be modified and encrypted by anyone else.
How much data can I store in The Vault?
Our data center in the Netherlands is designed so that we can expand all the time so there is no limit to the amount of data you want to safely park.
How is The Vault connected to my system?
The Vault Box (an SMB network drive) is linked to your backup system and The Vault itself. Using your backup software or our The Vault software, a replica of the backup data is created and it is passed to The Vault.
Can IMMUTEC retrieve files from The Vault for me?
No, we cannot access, read or delete the dataset we receive from you. The file is created by your backup system. In doing so, there will be a password on the data package, we do not have that password. Only you yourself.
Can I have a dataset removed from The Vault?
Yes, this is possible but can only be done through a special procedure that must be started if desired.
The signing authority of your institution/organization must confirm in writing that data may be removed from The Vault. Two of our engineers will then physically go to the data center and through a multi-step authentication together, manually delete the data.
How is the price of The Vault calculated?
We calculate the price based on your data set. That is; the dates you select to park in The Vault indicates the price associated with it. So you can check and calculate for yourself how much The Vault will cost.
What should I do if I am a victim of a ransomeware attack?
In a ransomware attack, a number of processes will need to be started simultaneously. If all goes well, your organization/institution will have a script for this. Have you not? IMMUTEC can support this.
IMMUTEC can also provide support after a ransomware attack. We then take a baseline measurement of your environment and incorporate that into our ” Rescue Plan” twice a year we update together so that we have a good picture of the organization.
In the event of a disaster or attack, our director springs into action and puts several teams to work to stop the attack and clean the systems again. Once the environment is clean again, we can use THE VAULT to restore the dataset and the backup system can be restored.
Contact us before you need us.
Our specialists will be happy to help you.
