Your own customized cybersecurity center
24/7 Managed XDR & Incident Response
The Tailored SOC (Security Operations Center) is a powerful cybersecurity and data protection solution. Through a combination of reactive and proactive approaches, your data is superbly protected.
The Tailored SOC is designed to proactively detect, analyze and respond to threats in your organization’s digital (IT) environment. While a cyber attack or data theft can never be completely prevented, the Tailored SOC solution makes it almost impossible. On one hand, every effort is made to keep hackers out, while on the other hand, it guarantees that you will always have access to your data, should anything happen.
The unique solution offers peace of mind thanks to total care and optimal protection.
24/7 Managed XDR
Incl. incident response within 1 hour
Fixed price per month
Complete Transparency: built in your own environment
We create a crisis plan together
Incl. IT health check in advance
Tailored SOC
Here’s how the Tailored SOC works
Detection provides 24/7 monitoring and alerting of (potential) threats

A security analyst proactively looks for possible threats (threat hunting) in your environment

In the event of an emergency, our emergency service will be notified

The emergency service engages the automatic SOC to stop the process or quarantine the object

The security analyst checks if everything has been done correctly, or if further actions may be needed
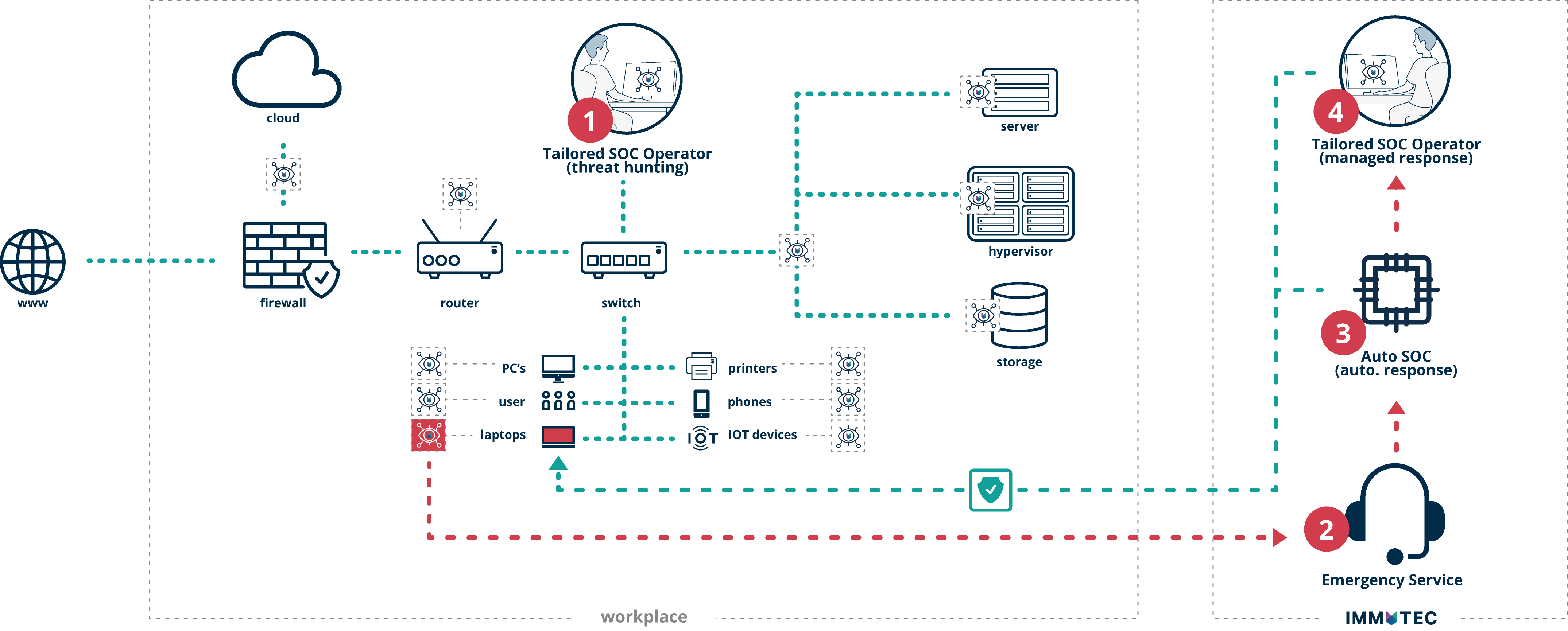
Tailored SOC in a nutshell
Automated Network Monitoring
Automated SOC
Endpoint Monitoring
Professional support
Built in your infrastructure
Managed Network Monitoring 24/7
Managed Incident Response
4 layer detection
Drafting crisis plan
IT Health Check
1-hour response time
Customized solution
Various contact moments with explanations, advice and explanations
Decrease possibility of Forensic examination (post-calculation)
FAQ Tailored Soc
What is a SIEM/SOC solution?
A SIEM-SOC solution helps organizations continuously monitor the security of their digital environment, identify potential threats and respond quickly to minimize the impact of security incidents. It is an important a powerful tool for the digital security of organizations.
The Security Information and Event Management (SIEM) acts as a digital security hub. It collects data from various sources, such as computers, servers, networks, and security devices, such as firewalls and antivirus software. The SIEM then analyzes this data to identify suspicious patterns, behaviors or anomalies that may indicate security problems. This can range from unusual login attempts to malware activity. When the SIEM detects potential threats, it generates alerts and reports. These are forwarded to the SOC (Security Operations Center).
The SOC is like the crew of a security post. It consists of security analysts and experts who receive alerts and reports from the SIEM. They investigate them thoroughly and take measures to stop or reduce possible threats. If necessary, the SOC can also take further steps, such as reporting incidents to management or law enforcement agencies.
Why is backup not enough?
A backup solution backs up your files and documents. A hacker’s goal is to make sure that no longer works and that the data in your backup is encrypted or misappropriated. This ensures that you can no longer restore a backup or access your backup system yourself. The only solution you have then is to pay a ransom. Unfortunately, in 9 out of 10 cases, that’s not enough either and it remains to be seen whether all your data will be released again.
What should I do if I am a victim of a ransomeware attack?
In a ransomware attack, a number of processes will need to be started simultaneously. If all goes well, your organization/institution will have a script for this. You don’t have it? IMMUTEC can provide this.
IMMUTEC can also provide support after a ransomware attack. We then take a baseline measurement of your environment and incorporate that into our ” Rescue Plan” twice a year we update together so that we have a good picture of the organization.
In the event of a disaster or attack, our director springs into action and puts several teams to work to stop the attack and clean the systems again. Once the environment is clean again, we can use THE VAULT to restore the dataset and the backup system can be restored.
Contact us before you need us.
Our specialists will be happy to help you.
